Australia has become something of a Mecca for Crypto ransomware according to data from a number of security vendors.
In October 2014, security firm Websense, detected nearly two million instances of the malware variant known as Cryptolocker, 60 per cent of those were detected in Australia.
During November and December 2014, the company said it detected 1.2 million and 1.05 million events respectively. Again it found 60 per cent of those were targeted at Australian hosts.
According to Websense, these attacks resulted in more than $US27 million in ransom payments made in the first two months.
Websense engineering manager A/NZ, Bradley Anstis, said the company had been exploring why Australia was such a big target for these types of attacks.
“The largest variant of crypto ransomware in terms of numbers was Cryptolocker. There are a number of reasons it was so successful,” he said.
According to Anstis, one of these reasons was localised content and the apparent authenticity of emails greatly contributed to the success of the attacks.
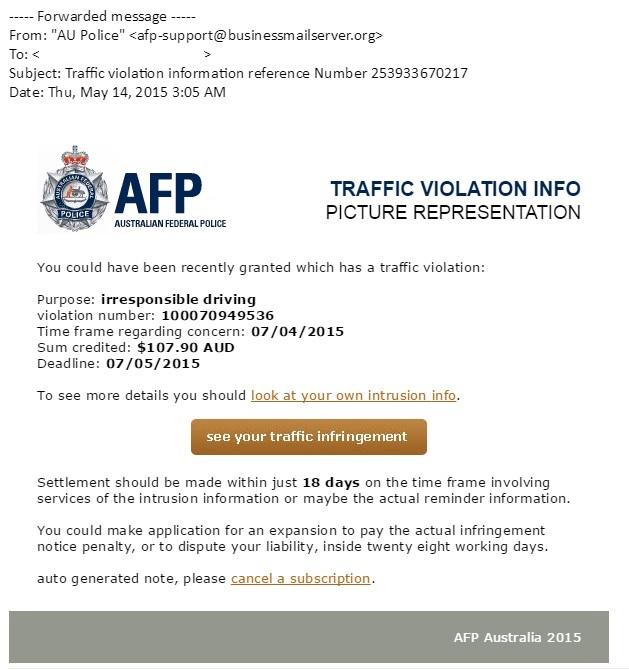
A similar threat was detected recently on April 28, forcing the Australian Federal Police (AFP) to send out an urgent warning to consumers to be wary of a fake email circulating throughout Australia and internationally that requests payment for a fake AFP Traffic Infringement Notice.
The scam email initially asked the recipient to pay an ‘AFP fine’ of approximately $150. If links within the message were clicked, the recipient’s computer was infected with malware which rendered it inoperable.
At that point, the ransomware was activated and the recipient was asked to pay thousands of dollars to reactivate their computer.
AFP National Coordinator Cyber Crime, Adrian Norris, said anyone who receives the email should delete it immediately.
“This email has taken off widely and looks legitimate, and many people have been compromised, so I would urge people to be vigilant,” he said.
“This email scam looks legitimate and contains AFP branding and may be from email addresses like TrafficInfringement.afp.org, TrafficInfringement.afp.com. or similar.”
A number of attacks last year came under the guise of the NSW State Debt Recovery Office (SDRO), and Australia Post. These emails enticed users to click on embedded links to pay a fine or receive information regarding package for collection.
Many users were caught by these scams and forced to pay fines in excess of $500.
“They are basically taking advantage of human nature. If someone believes they have a fine and thinks they have been hard done by, they will want to sort it out straight away,” Websense's Anstis said.
“Australia is also very attractive to cyber criminals. The exchange rate at the moment is very good and we are a wealthy country that makes us a big target.”
If the attacker was able to extract credit card or health information, that is worth three to four times more than payment of a simple ransom demand."
MailGuard founder and chief executive, Craig McDonald, said that in the most prevalent cases of crypto ransomware his company had observed in the last six to eight months, a large majority originate from Russia.
“Based on commonalities between various targeted campaigns, it appears to be a single group or a number working in tandem,” he said.
“These specific cyber criminals have great knowledge of the Australian systems. They have transitioned from a state based Government Authority (such as the NSW SDRO) to a national Government body (AFP).
“This is because they cannot identify the state of the email recipient, and so can now increase the chances of a victim clicking the link.”
Trend Micro Australia senior threat researcher, Dr. Jon Oliver, confirmed Australia was a big target per capita, but still lagged behind the US and other countries in terms of total incidents.
“In total volume, places like the United States dwarf us. However, per head of population it is safe to say we are a top target,” he said.
“When we do a distribution breakdown by country, Australia is regularly right up there with countries that have significantly higher populations.
“Australia ranks highly as a target in terms of absolute volume compared to England, Germany, Spain and Turkey.
“I can say with extraordinary confidence that, per head of population, Australia is the ransomware target.”
Oliver explained that there are three main families of crypto ransomware currently in use by cyber criminals. Cryptowall, Crypto CPB (sometimes referred to as CTB-Locker) and Torrentlocker. All these are either derived from, or were inspired by the very successful Cryptolocker that had its infrastructure knocked out by authorities in 2014.
“Torrentlocker targets Australia ferociously,” Oliver said.
“Torrentlocker actors go to special effort to tailor attacks to Australian victims.
“The attack purporting to be the AFP were the most frequent attacks that we have seen. For five days last week, the attacks were ferocious. They came on May 7, 8, 12 13,14 and 15 with huge frequency.”
Oliver noted that many of these attacks had also come under the guise of courier companies such as Couriers Please.
“In no way are any of these entities responsible in any way. They are victims too,” he said.
Oliver said that attackers using Torrentlocker had been quiet during January and the start of February in the leadup to the recent crypto ransomware blitz.
“There were other types of crypto ransomware appearing during that time, but it was sort of low level. They went up in March, down in April and May has been bedlam,” he said.
“It becoming IT managers greatest concern at the moment.
“We have really upped our spam alerts. Normally we don’t send out advisories for spam otherwise we would be sending 15 per day, but the ransomware spam is sufficiently notable.
"It takes such a toll on its victims that we are sending out alerts that are not vendor specific. We are sending them out because there is such a concern.
“The operational capabilities of those executing the attacks is very high,” he said.
“They have a deep understanding of the security solutions and how to evade them."
A high number of such attacks in the last six months have been perpetrated through the use of malware kits. Numbers vary depending on security vendor, but for a time, selling what some have termed “Malware-as-a-Service” was extremely popular amongst cyber criminal gangs.
Oliver believes the latest spate of attacks does not fit this pattern.
“I think its more sophisticated than that. If it was a kit, there would be diversity, the actors would be using rented facilities, things like botnets and pieces of cybercriminal infrastructure. We are not seeing anything like that with these torrentlocker outbreaks," he said.
“This particular attack targets Australia and Southern Europe. It targets Turkey, Spain, Italy and has recently moved to Germany, The UK and Poland. They seem to alternate their focus every 12 hours between Australia and Southern Europe.”
Symantec senior principal systems engineer (security), Nick Savvides, said the figures coming out of his own labs confirmed much of the data reported by other vendors.
“Last week, it was all about crypto malware attacks here in Australia,” he said.
“The AFP infringement notice had a massive run and that one was interesting because it contained really bad grammar but people were still falling for it.
“What was most interesting about that one, and it reflects the way these actors are using technology, is the rapid pace at which they bring up domains that host the crypto malware and how quickly they change through them.
“We are definitely one of the most targeted countries in the world. A lot of these variants are specifically targeted to the banking and finance sectors in Australia. Almost all of those we capture are enabled for Australian financial institutions."
According to Symantec’s raw data, Australia ranks seventh globally for ransomware incidents and first in the Asia Pacific and Japan (APJ) region.
“It depends on how you analyse that data,” Savvides said.
“We would definitely be in the top two in terms of revenue these guys manage to get out of a country.
In 2012-13, Symantec saw a 1400 per cent increase in incidents of crypto ransomware. Those figures came from a small base, but 2013-14 it detected a further 113 per cent increase in the number of ransomware incidents, showing that Australia is increasingly attractive to cyber criminal gangs using crypto malware.
“You are talking about an extremely high number of infections,” Savvides said.
“These guys are using local language, they are very focussed, they know how to communicate and they exploit Australia because we are trusting.
“We do a lot of online shopping in Australia so the parcel scams are very popular and extremely successful because we have the ability to pay.
“That’s why we are significantly over represented on a per capita basis and on a regional basis."
Savvides went on to concur with Anstis, Oliver and McDonald by emphasising the increasing sophistication of these attackers.
“They are using shadow services via Tor to hide their BItcoin payment gateway and they are offering great assistance to victims to help them pay.”
The majority of demands for payment from ransomware are for Bitcoin.
Savvides also said the newer types of crypto ransomware use a different encryption key for each file they encrypt instead of one key to lock down an entire system. This means that it is even more difficult for individuals or businesses to circumvent the encryption of files on a single machine or on a network.
Victims of such scams are strongly encouraged to report any incidents to the Australian Cyber Crime Online Reporting Network (ACORN) or Scamwatch.